A library for generating tripcodes on textboards and imageboards.
- Crack Tripcode
- Crack Trapcode Particular
How To Crack A Tripcode. Download Undangan Elegan Format Corel. Most Viewed Pages. Nch Express Scribe Keygen Crack; El Trueno De La Justicia Pdf.
Compatibility
This crate is compatible with tripcodes of the following formats:
As of Aug 2020, a normal tripcode could potentially be cracked in the timespan of a few hours and “secure tripcodes” in the timespan of weeks with lots of $$$$$. 'Super secure tripcodes” are not feasible to crack even with $$$$$. If anyone would like a custom tripcode, READ THIS! Maximum 5 letters. So, take my tripcode for example. Also, for him to 'create' you a code, he basically has to work through and 'crack' it for you. It gets harder and harder, exponentially, for him to use more and more of the code for you. A tripcode is the hashed result of a password that allows one's identity to be recognized without storing any data about users. Entering a particular password will let one 'sign' one's posts with the tripcode generated from that password.
- 4chan's normal (non-secure) tripcode
- 2channel's tripcodes:
- 10-character tripcode (10桁トリップ)
- Nama key tripcode (生キートリップ)
- 12-character tripcode (12桁トリップ)
- 2ch.sc's tripcodes:
- 15-character tripcode (15桁トリップ)
- Katakana tripcode (カタカナトリップ)
Usage
Add tripcode to the dependencies in your project's Cargo.toml:
and this to your crate root:
Overview
Basic examples:
Handling non-UTF-8 passwords
Besides str, the generate() method can take any object that implements AsRef<[u8]>so that it can handle non-UTF-8 passwords.
Here's an example of generating a tripcode from a CP932 (superset of Shift-JIS) encoded password.This example uses encoding crate:
Avoiding reallocations
The append() method takes a &mut String and appends the resulting tripcode to it.The method does not cause additional heap allocations if the buffer has sufficient capacity tostore the tripcode.

Writing to streams
The write() method takes a mutable reference to a Write and writes the resulting tripcodeto it.
Reexports
pub use FourchanNonescaping as Mona10Nonescaping; |
Modules
| hash | Tools for handling lightweight hash values that can be encoded to/decoded from tripcodes. |
Structs
| Des | Generator for DES-based tripcodes (4chan and 2channel's 10-character tripcode)that accepts custom salt characters. |
| Fourchan | Generator for tripcodes on 4chan. |
| FourchanNonescaping | Same as Fourchan and Mona10 except that it does not escape HTML special charactersin passwords. |
| Mona | Generator for tripcodes on 2channel. |
| Mona10 | Generator for 2channel's 10-character tripcodes (10桁トリップ). |
| Mona12 | Generator for 2channel's 12-character tripcodes. |
| Mona12Nonescaping | Same as Mona12 except that it does not escape HTML special characters in passwords. |
| MonaNonescaping | Same as Mona except that it does not escape HTML special characters in passwords. |
| MonaRaw | Generator for 2channel's nama key tripcodes (生キートリップ). |
| Sc | Generator for tripcodes on 2ch.sc. |
| Sc15 | Generator for 2ch.sc's 15-character tripcodes (15桁トリップ). |
| ScKatakana | Generator for 2ch.sc's katakana tripcodes (カタカナトリップ). |
| ScSjis | Same as Sc except that it treats passwords as Shift-JIS-encodedwhen generating katakana tripcodes. |
Traits
| TripcodeGenerator | Trait for generators of tripcodes. |
| TripcodeGeneratorFailable | Trait for tripcode generators which may fail in generation. |
My Authors
Many people have been asking me about tripcodes in the past week. Initially I was planning to write a document detailing the different types of tripcode, but have decided a tweet chain will allow for more engagement.
In August 2001, the first generation of the tripcode algorithm was designed and coded by FOX for the 2channel anonymous BBS using the perl crypt() function. Tripcodes were meant to be portable anonymous identities to be shared across sites that deployed the same algorithm.
A normal tripcode using the 2001 algorithm will display a single “!” before the tripcode text itself. Initially, the length of tripcode output in the original algorithm was 12 characters, then was adjusted to 8, and finally re-adjusted to the current 10 character length.
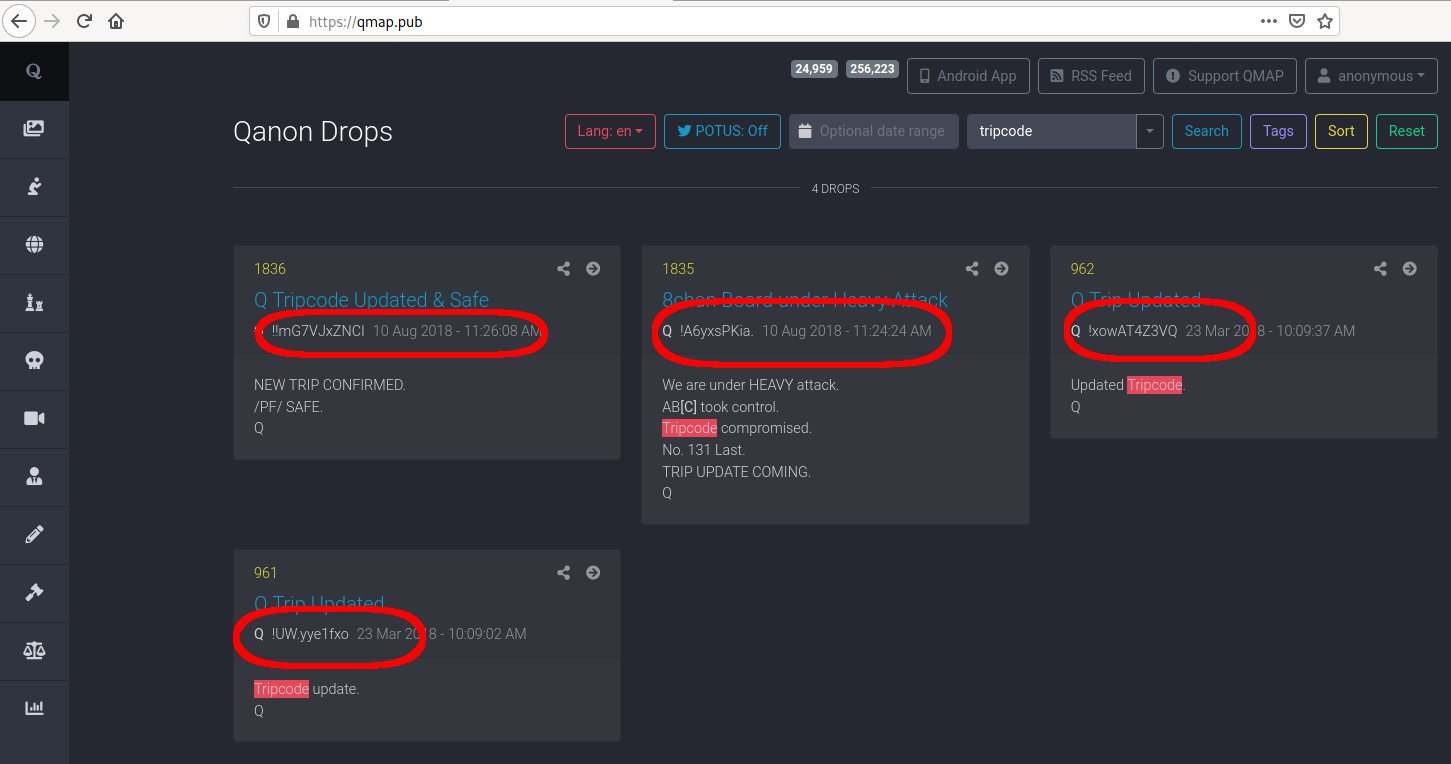
Not long after the introduction of the tripcode, the lack of server-side salt in the original algorithm caused end-users to be concerned about bad actors cracking tripcodes. Several attempts were made to create a “secure” tripcode which utilized a server-side salt.
Server-side salts are random data that gets mixed behind-the-scenes with your initial input data and is used to help make the hash less susceptible to attacks. Sharing a salt publicly is effectively the same as having no salt at all.
Crack Tripcode
Since a “secure” tripcodes rely on a server side salt, a secure tripcode is not portable and can’t be used across sites that deploy the same algorithm unless any salts are shared also. Sharing salts defeats the purpose of having a salt in the first place.
“Secure tripcodes” don’t require an open standard and different sites have implemented them in different ways. A “secure tripcode” is generally prefixed with a double exclamation mark “!!”.
OpenIB’s software implementation of “secure tripcodes” is based on the sha1 algorithm. Finding a sha1 hash collision can technically be bruteforced in 2020, but would potentially require access to the server-side salt and a large amount of money ($$$$$) to do so.
It has recently come to my attention that it is also possible to brute force the secure tripcode salt used in OpenIB, but there is no indication that this has happened as of August 2020. The monetary resources required to do so could potentially be very large ($$$$$) also.
“Salt rotation” happens periodically on our site and means we regenerate the server-side salt with the intention of preventing bad actors from brute forcing any hashes they might be targeting. After a “salt rotation”, any secure tripcode become completely different.
In 2018, I made a third generation tripcode algorithm called the “super secure tripcode” (or SST) for short. The SST uses the sha256 hash algorithm and a server-side salt with the intention of providing a hash that cant feasibly be cracked even if the server-side salt was leaked.
Crack Trapcode Particular
“Super secure tripcodes” use a triple exclamation mark (!!!) prefix and are 16 characters in length.
As of Aug 2020, a normal tripcode could potentially be cracked in the timespan of a few hours and “secure tripcodes” in the timespan of weeks with lots of $$$$$. 'Super secure tripcodes” are not feasible to crack even with $$$$$.
Disclaimer: Im not a professional security researcher (though I did study netsec in grad school almost a decade ago), so if I made any mistakes with this write-up, please correct me in the comments. Thanks for spending the time to read this.



